.__ __________
| |__ ____ _____ ____\______ \__ _ ______
| | \ / _ \ / \_/ __ \| ___/\ \/ \/ / \
| Y ( <_> ) Y Y \ ___/| | \ / | \
|___| /\____/|__|_| /\___ >____| \/\_/|___| /
\/ \/ \/ \/
☠ HomePwn - IoT Pentesting & Ethical Hacking ☠
Created with ♥ by: 'Ideas Locas (CDO Telefonica)'
HomePwn is a framework that provides features to audit and pentesting devices that company employees can use in their day-to-day work and inside the same working environment. It is designed to find devices in the home or office, take advantage of certain vulnerabilities to read or send data to those devices. With a strong library of modules you can use this tool to load new features and use them in a vast variety of devices.
HomePwn has a modular architecture in which any user can expand the knowledge base about different technologies. Principally it has two different components:
-
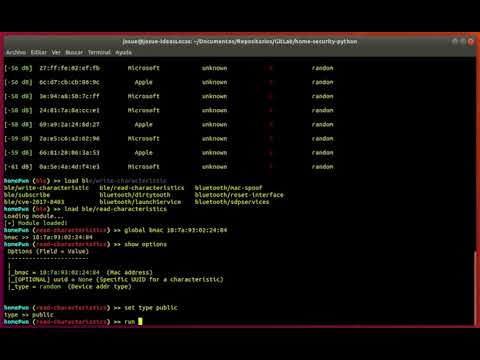
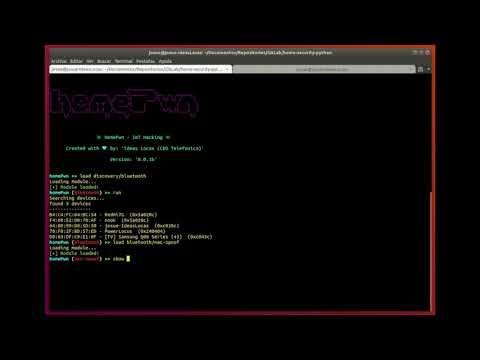
Discovery modules. These modules provide functionalities related to the discovery stage, regardless of the technology to be used. For example, it can be used to conduct WiFi scans via an adapter in monitor mode, perform discovery of BLE devices, Bluetooth Low-Energy, which other devices are nearby and view their connectivity status, etc. Also, It can be used to discover a home or office IoT services using protocols such as SSDP or Simple Service Discovery Protocol and MDNS or Multicast DNS.
-
Specific modules for the technology to be audited. On the other hand, there are specific modules for audited technology. Today, HomePwn can perform auditing tests on technologies such as WiFi, NFC, or BLE. In other words, there are modules for each of these technologies in which different known vulnerabilities or different techniques are implemented to asses the device's security level implemented and communicated with this kind of technologies.
- Python - Programming language used
- Prompt Toolkit - Python command line
It's possible to read the documentation in our papers:
These instructions will get you a copy of the project up and running on your local machine for development and testing purposes. See deployment for notes on how to deploy the project on a live system.
You need to have Linux and python 3.6+ running in your computer, please install them in the download page.
- Ubuntu, Debian or similar.
- Python 3.6+.
To install all dependencies in Ubuntu 18.04 or derivatives use the file install.sh
> sudo apt-get update
> cd [path to the HomePWN project]
> sudo ./install.sh
The script ask you if you want to create a virtualenv, if your answer is 'y' then it installs python libraries within the virtual environment, if not in the system itself
To run the script, if you chose a virtual environment in the installation follow execute the next command to activate the virtual environment:
> source homePwn/bin/activate
Launch the application:
> sudo python3 homePwn.py
https://askubuntu.com/questions/1122095/install-alfa-awus036nha-driver-on-ubuntu-18-04-lts
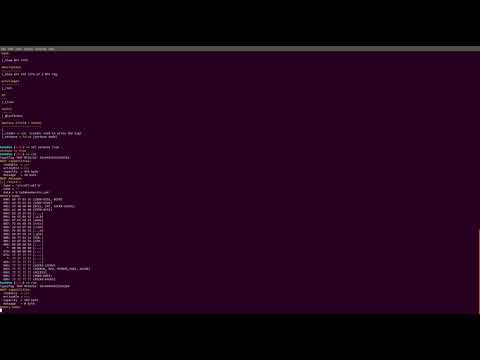
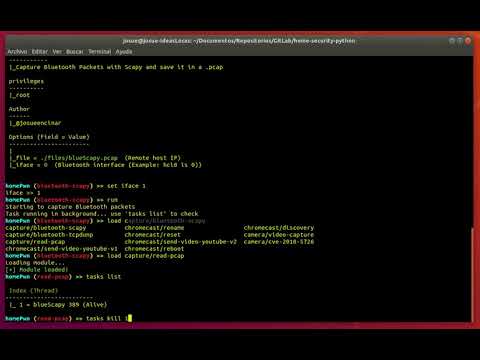
Here are some videos to see how the tool works.
This project has been developed by the team of 'Ideas Locas' (CDO - Telefónica). To contact the authors:
See also the list of CONTRIBUTORS.md who participated in this project.
Please read CONTRIBUTING.md for details on our code of conduct, and the process for submitting pull requests to us.
This project is licensed under the GNU General Public License - see the LICENSE.md file for details.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE. WHENEVER YOU MAKE A CONTRIBUTION TO A REPOSITORY CONTAINING NOTICE OF A LICENSE, YOU LICENSE YOUR CONTRIBUTION UNDER THE SAME TERMS, AND YOU AGREE THAT YOU HAVE THE RIGHT TO LICENSE YOUR CONTRIBUTION UNDER THOSE TERMS. IF YOU HAVE A SEPARATE AGREEMENT TO LICENSE YOUR CONTRIBUTIONS UNDER DIFFERENT TERMS, SUCH AS A CONTRIBUTOR LICENSE AGREEMENT, THAT AGREEMENT WILL SUPERSEDE.
This software doesn't have a QA Process.